Configuration management has long been a challenge for administrators. From security settings to software installation to web browser settings, IT staff members have needed to control user systems to provide the tools the users need without giving access to features that weaken security or generate support issues.
Microsoft introduced Group Policy alongside Active Directory with Windows 2000. Its basic function remains the same, though the number of settings it manages has greatly increased.
Consider the following uses:
- Security settings: Password requirements, group memberships, firewall port configurations, IPsec settings and more.
- Software management: Allowed/disallowed applications, application installation and program settings for tools such as Office.
- Desktop configuration: Available desktop icons, start menu settings, Control Panel access, File Explorer views and more.
This list of configuration requirements is impressive, but Group Policy can do far more.
One essential aspect of Group Policy is giving users the tools they need. Too often, Group Policy is described as a way of curtailing user choices and options, but it's just as important to recognize it as a tool that configures Windows with the tools the users need to do their jobs.
How can Group Policy help?
Group Policy provides access to thousands of settings on Windows computers that are domain members. It also provides a comprehensive set of configuration options for standalone non-domain Windows systems using Local Policies.
The primary administrative tool is the Group Policy Management Console, accessible via the Administrative Tools link in Server Manager or through Administrative Tools installed locally on an administrator's workstation.
When opening the console, it displays the domain, OUs, and sites in a tree on the left. Selecting objects in this pane changes the view of the right-hand pane.
Configurations are collected in sets called Group Policy Objects (GPOs). GPOs are stored in a specific Group Policy Objects node in the console's left pane.
GPOs are collections of related settings. The essential word in that description is related. GPOs are usually subject-oriented, with settings that logically go together. For example, you might create a "Desktop Configuration GPO" that contains desktop and Start menu settings, then a different "Network Configuration GPO" that has (you guessed it) network settings. Collecting similar settings into GPOs makes understanding the policy's purpose easier, improving design and easing troubleshooting.
Consider the following three GPO examples.
1. Default domain policy
The first GPO to understand is the Default Domain Policy. This GPO is created with Active Directory and manages domain password settings. It forces you to change your password every 90 days (or whatever your organization deems appropriate), requires 12-character passwords, and prevents you from repeating passwords frequently.
Microsoft recommends only using this GPO for password settings. I used to teach it to students as the "Default Password Policy."
2. Security settings
An administrator might then choose to create their own security-oriented GPO. For example, the company's security policy might require the following settings:
- Clear username from the login box
- Show security warning message on login
- Rename the local administrator or guest accounts
- Disable the local administrator or guest accounts
- Restrict access to Regedit
- Restrict access to Control Panel applets
What's not in this GPO is just as important. No software deployments, Start menu options, or display settings are included in this policy. Those settings are not related to security concerns, so you should place them in a different GPO.
3. Software deployment
Many tools exist today for deploying and managing software. Group Policy is especially useful for simple deployments, though it does offer features for complex installers that request user input.
Group Policy can launch MSI package installations and call answer files to provide settings to application setup wizards. The software can be deployed to computers (making the application available to any user at the computer) or to users (providing the application to a user regardless of which computer they're logged in to).
Create a GPO
Use the following steps to create a new GPO that you will later link to a Site, the domain or an Organizational Unit.
1. Right-click the Group Policy Objects node and select New.
Figure: To create a new GPO, right-click the Group Policy Objects node
2. Give the new GPO a descriptive name.
Figure: Name the GPO
3. You may now edit the GPO, defining whatever configurations are needed.
Figure: Edit the GPO to configure settings
Link a GPO
Once you have defined the settings you want for this GPO, it's time to link it to its target users or computers.
Administrators link GPOs to active directory sites and domains or organizational units to apply group policy settings to users and computers. These three components provide different scopes of user controls.
You cannot link GPOs to individual user or computer accounts or Active Directory Global or Domain Local groups.
To link a GPO, right-click the Site, domain or OU to which the setting should apply. For example, to apply a GPO to the Sales OU, follow these steps:
1. Right-click the Sales OU and select Link an Existing GPO.
2. Select the GPO you wish to apply.
3. Select the OU to see any linked GPOs.
I've deliberately listed the components above in order based on how Group Policy settings are applied. When a user and computer authenticate against AD, local policies are applied first, followed by any policies linked to the site where the user and computer log in, policies linked to the entire domain, and finally, policies linked to OUs (and child OUs).
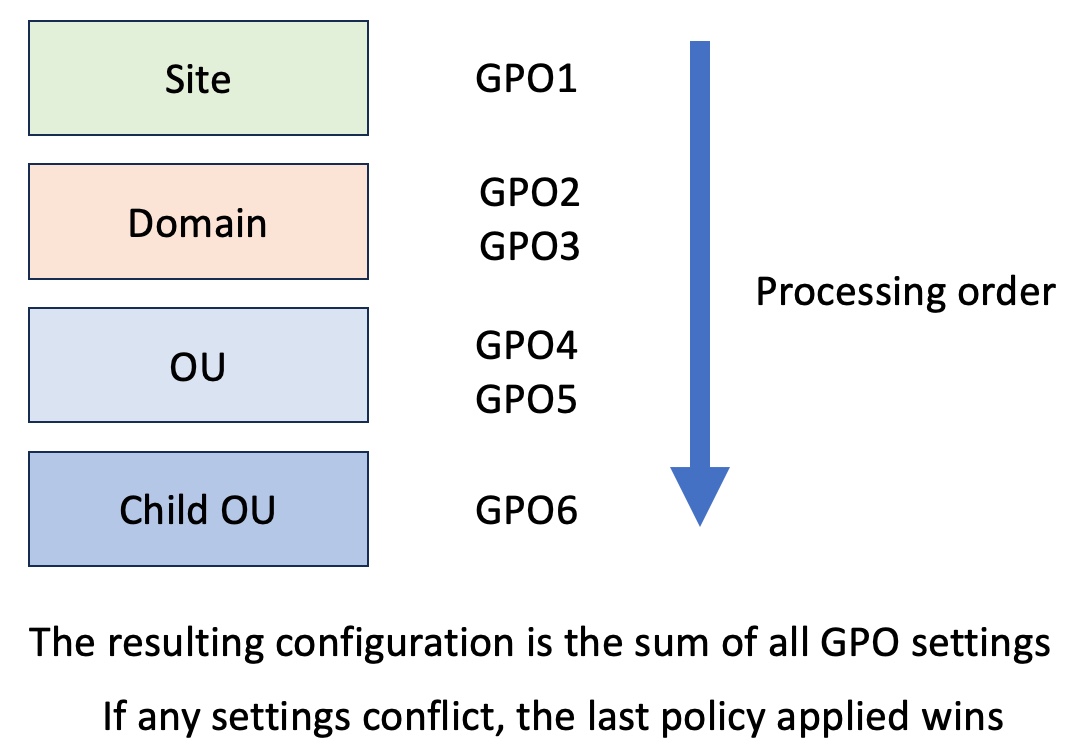
Figure: Group Policy application order
Any policy conflicts are resolved based on the idea that the last policy applied wins. For example, if a site GPO sets a green desktop wallpaper, then a domain-linked GPO sets a red wallpaper, and a GPO at the OU level sets a blue wallpaper, the final result is blue because the OU policy was applied last.
Group Policy precedence (the order of events for conflicting policy settings) can be much more complex, but this is the basic flow, and it's useful for troubleshooting. I am careful to discuss GP applications in the order of Site, domain, and OU to help reinforce this precedence.
GPOs linked to AD Sites are pretty uncommon. These GPOs contain settings specific to a company location, such as wireless network settings or print device mappings.
GPOs linked to the domain provide company-wide settings. These settings apply to all users and computers, regardless of department or role. The settings are broad, generic configurations, such as setting the company logo as the desktop wallpaper for all computers.
OU-linked GPOs are for department-specific settings. For example, I might have a GPO deploying programming applications linked to the Developers OU and a different GPO deploying sales resources to the Sales OU.
Planning and troubleshooting Group Policy
Microsoft provides several tools to plan and troubleshoot Group Policy. These are built-in utilities; others are available online.
Planning for Group Policy
The Group Policy Modeling Wizard allows you to see the results of "what if" scenarios. For example, what would the resulting application of GPOs be if a GPO were linked to a given OU, from a given site, with various permissions levels and a slow WAN connection? The report shows the resulting GPO-configured settings.
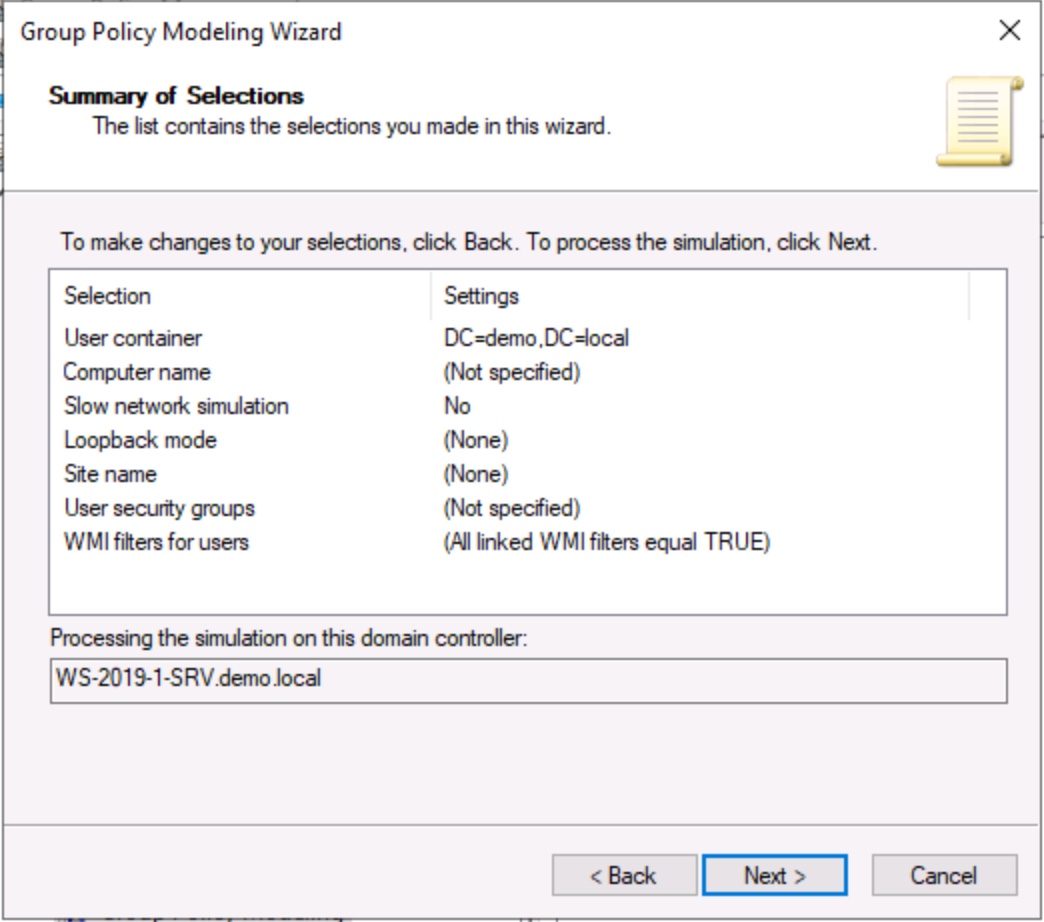
Figure: Summary of selections for the Group Policy Modeling Wizard
Use the Modeling Wizard to predict results before making major GPO changes.
Troubleshooting Group Policy
Administrators can troubleshoot Group Policy from the Group Policy console using the Group Policy Results Wizard or the client system using the gpresults command.
The Group Policy Management Console includes a Group Policy Results Wizard. This tool lets you specify users and computers to see what GPO settings apply. While the GP Modeling Wizard is a planning tool (it shows what would happen), the GP Results Wizard is a troubleshooting utility (it shows what is happening).
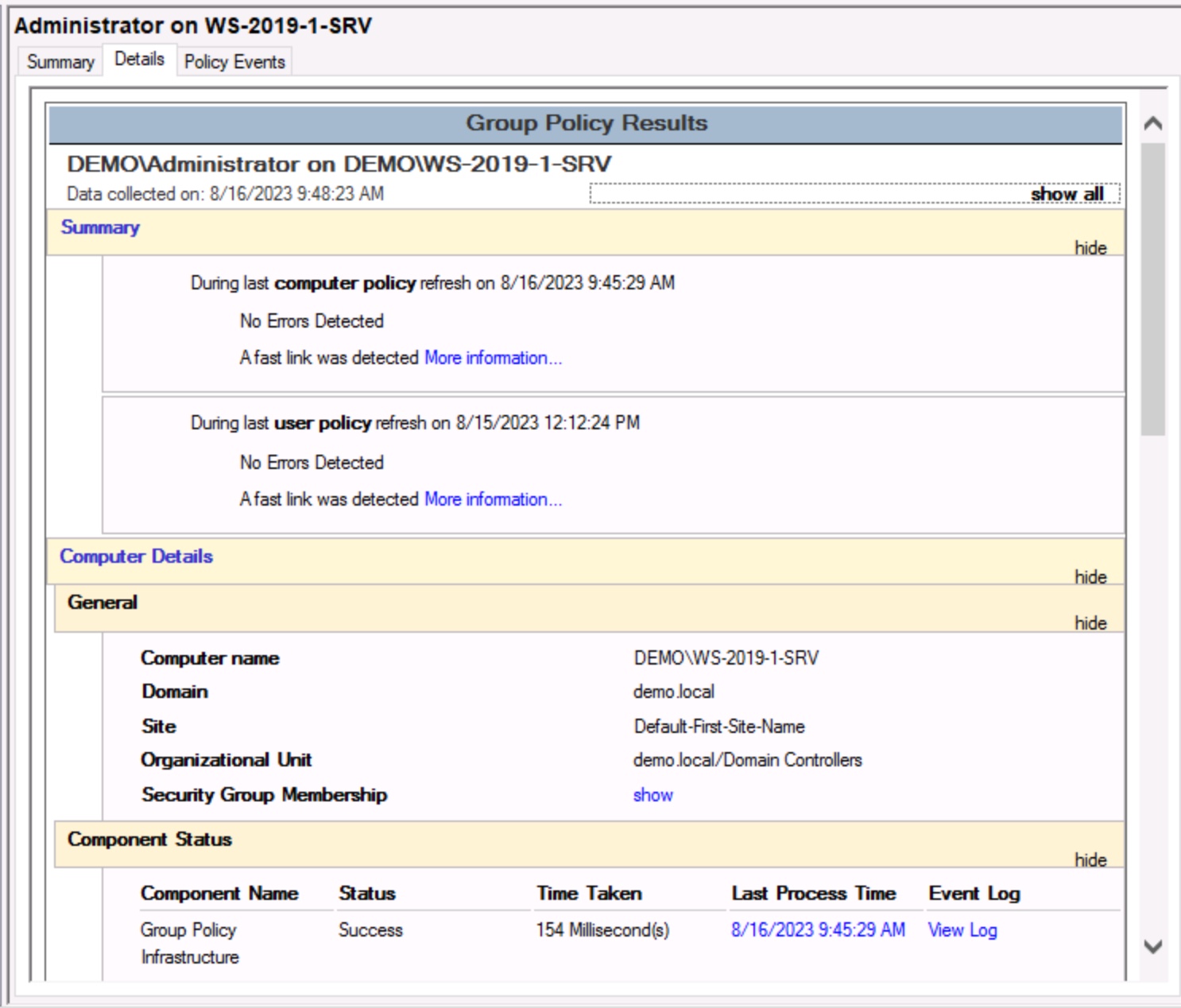
Figure: The Group Policy Results Wizard
One of the most useful Group Policy troubleshooting tools is the gpresult command. This command displays the GPOs and settings that have been applied to the system. While the precedence order and other factors help you predict what settings should be applied, this tool shows you what settings are applied. You can backtrack from there to discover why expected configurations aren't present.
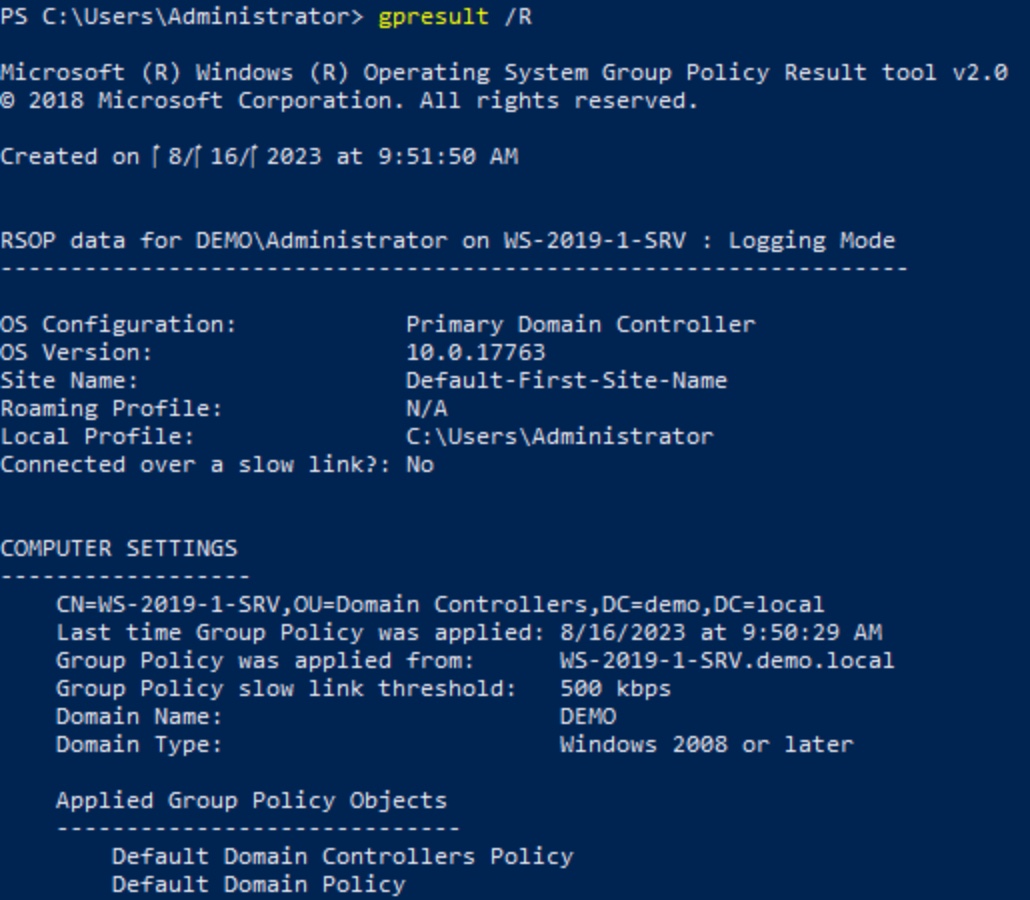
Figure: Partial results from the gpresult command
The above screenshot shows a subset of the report generated by the gpresult command. Notice that it includes which GPOs are applied (the Default Domain Controllers Policy and the Default Domain Policy). It also provides information on when the policies were last refreshed and from which Domain Controller.
The gpresult command is run from the client system, usually during troubleshooting. The Group Policy Results Wizard is run from within the Group Policy Management console on a Domain Controller.
Managing Group Policy
I distinctly remember troubleshooting a Group Policy problem in the small Active Directory network I managed. The user asked about a missing setting, so I went to their workstation and confirmed it using gpresult. Then I returned to the Group Policy console on the Domain Controller and found the problem. I corrected the setting in the GPO, but how could I refresh the policies on the user's system?
To complete the configuration, I returned to the user's system and typed the gpupdate /force command.
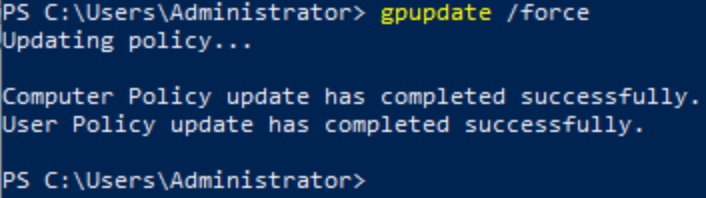
Figure: The gpupdate command
There are several options for updating or refreshing Group Policy settings:
- Reboot the system two to four times: Thanks to policy caching, it may take up to four reboots to refresh a policy. If the policy is linked at a level requiring user and computer authentication, each reboot also requires logging in.
- Use the gpupdate command: Return to the user's workstation and run the gpupdate command. However, again thanks to policy caching, this command may not be enough. The basic gpupdate command compares the current policies on the system to the policies on the server. Notice that that's not the same thing as reapplying the policies! Add the /force switch to gpupdate to bypass this comparison and reapply the policies, whether or not they've changed.
- Group Policy Update: New to Windows Server 2012's AD version, administrators can now push policy refreshes from the Group Policy console. This method may not be as quick for an individual system as using gpupdate /force, but it's much faster for a large group of machines.
Slowly start working with Group Policy
Many administrators deploying Active Directory for the first time assume they'll create a domain, build some OUs and worry about Group Policy later. This isn't the right approach. Group Policy settings link to OUs to deliver department-specific configurations. It's usually best to design your OU structure around how you intend to use Group Policy.
GPOs at the domain level provide company-wide settings that should apply to all users and computer accounts. These settings often include security settings, general desktop configurations, blocking or providing access to Windows features, etc.
Begin working with Group Policy using small sets of changes. Remember that GPOs are collections of related settings—it's difficult to understand and troubleshoot GPOs filled with seemingly random choices.
Group Policy is one of the most powerful and practical tools in Active Directory. Maximizing its efficiency, design and use makes configuration management easier. It takes away components that might cause issues for users and provides the tools they need to do their jobs. Investigate your Group Policy deployment today to see how you can improve it!
Ready to upgrade your IT skills? Explore CompTIA certifications and training right now.