As I mentioned in my last article about password security, minimal risk employees who understand IT security risks and take action to prevent them are a critical piece to the IT security puzzle. After setting policies about how to choose passwords and when to update them, helping them to identify fake email addresses and URLs gives end users the power to be vigilant against cybersecurity threats.
Proactive training is a critical step in equipping every employee to play their part in a cybersecurity strategy. In this article, we will cover how to identify fake email addresses and fake websites and offer some pro tips for better security awareness training.
How to identify fake email addresses
Where is your email coming from? Fake email addresses attempt to trick end users into a sense of comfort, security, and legitimacy. Does the domain from which you’re receiving the email make sense? Is it consistent with the organization’s domain?
Here are two ways to identify fake email addresses:
1. What comes after the @ sign?
As mentioned above, a legit email domain will match the URL for the organization’s website. Here are examples of safe and unsafe email domains:
- Safe: @chase.com
- Unsafe: @chasebank.com
At a glance, this seems like a reasonable and safe domain. But if the domain is anything different than what you would type in a web browser to access the organization’s website, it’s most likely a fraudulent email address.
2. What name appears in the email?
An internet user's real name means nothing when it comes to email communication. There’s no intellectual property or restrictions on the names of emails when creating an account. In fact, many legitimate businesses create fictional names for marketing emails that just head back to a distribution list so they can avoid being flagged for email abuse without opt-in policies.
Anyone can start an email account with someone else’s name, and there are no checks and balances to determine if it is legitimately the person sending it. That’s why the domain is so important—there’s a registration process for domains related to unique IP addresses, so it’s not possible to copy without having inside access.
Pro tip for email security awareness training
Utilize one of the many phishing awareness tools available today to both educate and test your users. Make sure this isn’t a one-and-done practice but something that occurs throughout the year. People forget or get distracted, and only with continuous training can they be aware.
How to identify fake websites
One of the easier ways to mitigate cybersecurity risk is to train your employees to pay attention to the address bar in their web browser.
Pay attention to the browser and ask the following questions to identify fake websites:
- Is your connection secure? Look to the far left of your address bar. If you’re using Safari, Chrome, or Firefox, you should see a padlock icon to indicate that your connection is safe.
- If you are still using Internet Explorer (IE), then you are at a large risk of falling victim to fake websites. Especially given Microsoft has officially retired IE. There are countless other browsers that are much safer, especially Firefox. Secure browsing can help mitigate issues with domain spoofing and other issues that can derive from malicious websites.
- Secure Socket Layer (SSL)/ Transport Layer Security (TLS) certificates are now easier for threat actors to get, so the “padlock” strategy isn’t effective enough on its own. The lock icon is not bulletproof, and it must be used in combination with the rest of the points that follow.
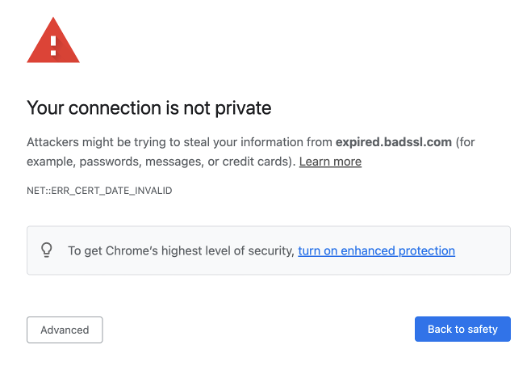
Stop if you get a message in your browser like this: “Your connection is not Private.”
It means there is something wrong with the SSL/TLS connection, and it shouldn’t be trusted. Where did the URL come from?
1. Does the URL make sense?
Use the same strategy to identify fake websites that you would to identify fake email addresses. The main parts of the URL before .com or .org, etc., should not be an alphabet soup of letters and numbers. The domain origination of the main site and emails that you receive from the organization should match.
A relevant example for personal banking would be:
- Safe: chase.com/creditcardoffer
- Unsafe: chasecom.ru/creditcardoffer
Threat actors purposely try to mask their URLs in clever ways, often by incorporating special characters or a combination of letters that resemble the correct website. If you’re not looking closely, you can easily be misled into clicking the link and installing malware on your device, even if the link doesn’t load or takes you to a dead page. Also, be aware that URL shortening is something that bad actors frequently use to hide a website's true URL, so be very careful when clicking them in posts or emails.
2. Did you get the link in an email?
If so, don’t click. This sounds extreme. It also sounds slow and antiquated. But verification is a pillar of being vigilant. Even if the contact emailing you is in your address book, they could have been phished—you just never know.
- Contact the contact before clicking. Calling is generally preferred. If you are emailing, make sure you open a new email to verify that the last email was legitimate. Replying directly to the email will put you in contact with the malicious sender, who will work diligently to mislead you.
- Do not open the email until you have contacted the sender. Especially if it’s from an internal source. This will only create a stronger cybersecurity culture. This training exercise is all about this step, even though it may seem unnecessary or slow. The more cybersecurity issues and awareness about them are widely discussed, the more it is prioritized in typical day-to-day interactions they will become even for not IT or security teams.
Check out the whole series on security awareness training:
- Passwords Are a Pain—But They Are Critical to IT Security
- What Does a Phishing Email Look Like?
- Why You Need a Corporate Acceptable Use Policy
- Incident Response Plans and War Gaming
- Network Segmentation
Ready to upgrade your IT skills? Check out CompTIA certifications and training.