Cybersecurity is no longer optional for state and local governments. With increasing cyber threats targeting public infrastructure and sensitive citizen data, agencies must adopt robust cybersecurity measures to protect their systems, maintain public trust, and ensure operational continuity. This guide outlines the top cybersecurity requirements, compliance mandates, and best practices to help government agencies stay secure and resilient.
Why cybersecurity is a priority for government agencies
Cyberattacks on state and local governments are on the rise, with ransomware, phishing, and data breaches becoming increasingly common. These attacks disrupt essential services, compromise sensitive information, and cost millions in recovery efforts. To combat these threats, government agencies must prioritize cybersecurity by adhering to compliance mandates, implementing best practices, and upskilling their IT teams.
In this blog, we’ll explore the top cybersecurity tips for state and local governments, provide actionable tips for compliance, and highlight the role of certifications like CompTIA Security+ and CySA+ in building a resilient workforce.
The top cybersecurity recommendations for government agencies
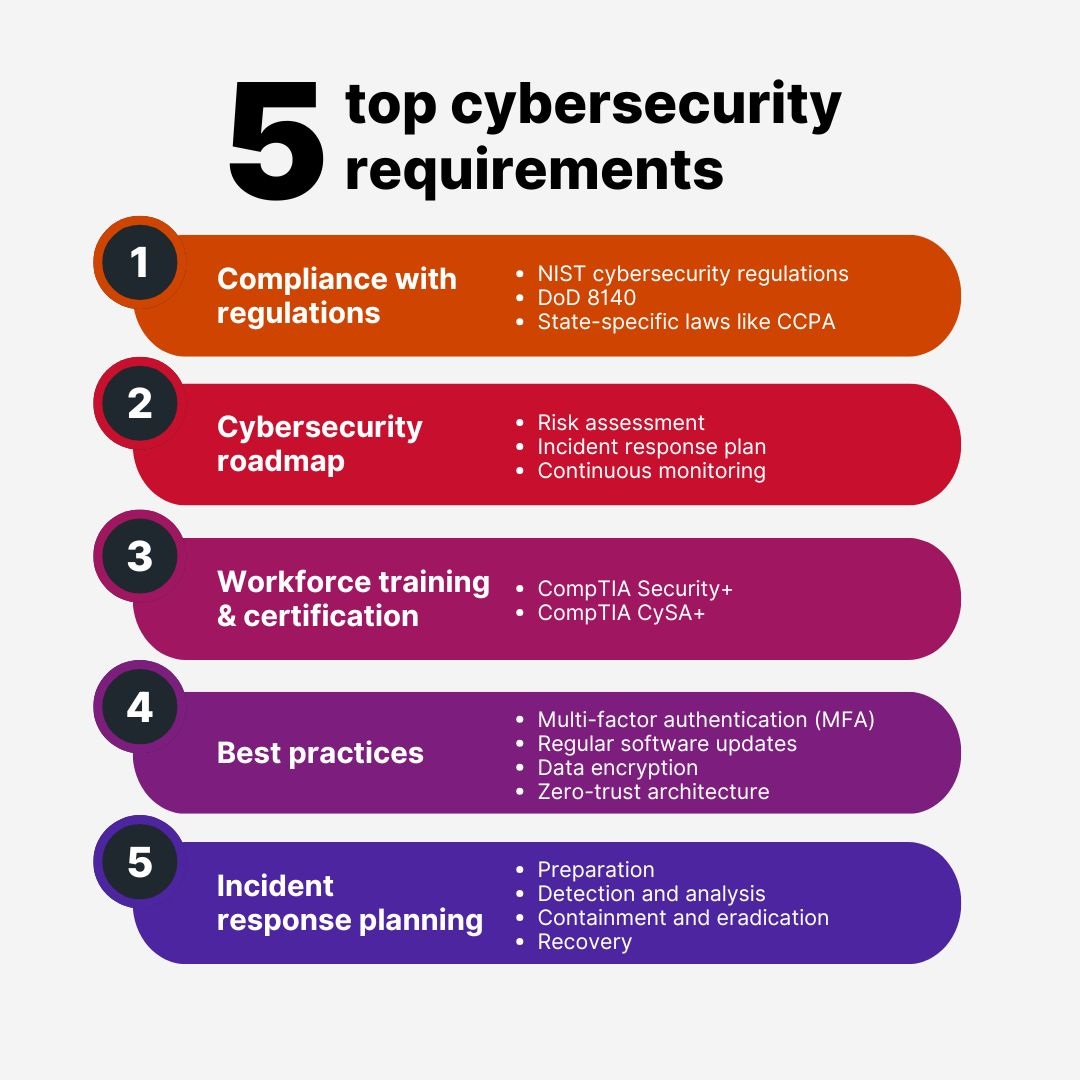
1. Compliance with federal and state cybersecurity mandates
State and local governments must comply with strict cybersecurity regulations to protect critical infrastructure and sensitive data. Key frameworks include:
-
- NIST Cybersecurity Framework (CSF): A comprehensive guide for managing cybersecurity risks.
- State-Specific Regulations: Laws like California’s Consumer Privacy Act (CCPA) enforce data protection and privacy standards.
Actionable Tip: Conduct regular compliance audits to identify gaps and ensure adherence to these frameworks.
Source: A Guide to Cybersecurity Compliance for State and Local Governments
2. Develop a cybersecurity roadmap
A well-defined cybersecurity roadmap is essential for identifying vulnerabilities, setting priorities, and allocating resources effectively. Key components include:
- Risk assessment: Identify and prioritize potential threats.
- Incident response plan: Establish clear protocols for responding to cyberattacks.
- Continuous monitoring: Use tools to detect and respond to threats in real-time.
Pro Tip: Train your IT team with certifications like Security+ and CySA+ to implement and manage a cybersecurity roadmap effectively.
3. Workforce training and certification
Human error is one of the leading causes of cyber incidents. Upskilling IT teams with relevant certifications ensures they are equipped to handle evolving threats. Recommended certifications include:
- CompTIA Security+: Covers foundational cybersecurity skills and compliance best practices.
- CompTIA CySA+: Focuses on advanced threat detection and response.
Actionable Tip: Prioritize training and certifications to equip your staff with the tools they need to safeguard sensitive data, maintain public trust, and ensure operational continuity.
4. Implementing cybersecurity best practices
Adopting best practices is critical for minimizing vulnerabilities and protecting systems. Key measures include:
- Multi-Factor Authentication (MFA): adds an extra layer of security to user accounts.
- Regular software updates: protects systems against known vulnerabilities.
- Data encryption: safeguards sensitive information from unauthorized access.
- Zero trust architecture: limits access to only those who need it.
Checklist: Download our Cybersecurity Compliance Checklist for State and Local Government to ensure your agency is following best practices.
5. Incident response and recovery planning
No system is immune to cyber threats, making a robust incident response plan essential. Key steps include:
- Preparation: Train staff to recognize and report incidents.
- Detection and analysis: Use monitoring tools to identify threats quickly.
- Containment and eradication: Isolate affected systems and remove the threat.
- Recovery: Restore operations and conduct a post-incident review.
Pro Tip: Regularly test your incident response plan with simulated cyberattacks to ensure readiness.
Lessons learned from government cybersecurity breaches
Real-world examples highlight the importance of robust cybersecurity measures:
Wichita, Kansas Ransomware Attack (2024)
The LockBit ransomware group targeted the city of Wichita, Kansas, disabling payment systems and even affecting the local airport’s Wi-Fi access.
- Impact: The attack caused significant disruption to city services and highlighted vulnerabilities in municipal IT systems.
- Source: Statescoop
Oakland, California Ransomware Attack (2023)
The city of Oakland suffered a ransomware attack that disrupted multiple government services, including access to public records and payment systems.
- Impact: The attack caused weeks of operational delays and exposed vulnerabilities in the city’s IT infrastructure.
- Source: Seculore
Dallas, Texas Ransomware Attack (2023)
- Details: The city of Dallas experienced a ransomware attack that impacted police and fire department systems, delaying emergency response times.
- Impact: The attack caused significant operational disruptions and raised concerns about the security of critical infrastructure.
- Source: Bleeping Computer
Key Takeaways from Recent Attacks
- Ransomware as a Service (RaaS): Many of these attacks were carried out by RaaS groups like ALPHV and LockBit, which lower the barrier for entry for cybercriminals.
- Operational Disruption: These attacks often target critical services, such as emergency response systems, payment platforms, and public utilities.
- Financial Impact: Recovery costs for these attacks often run into the millions, highlighting the need for proactive cybersecurity measures.
Why certifications like Security+ and CySA+ matter
Certifications play a vital role in equipping IT professionals with the skills needed to combat modern cyber threats. For example:
- Security+: Provides foundational knowledge in risk management, network security, and compliance.
- CySA+: Focuses on advanced threat detection and response, making it ideal for SOC analysts.
Actionable Tip: Invest in certifications and training to strengthen your agency’s security posture and empower your staff to protect critical infrastructure and maintain public trust. Take the first step toward a more secure future—start certifying your team today!
The consequences of non-compliance
Failing to meet cybersecurity requirements can have severe consequences, including:
- Financial costs: Recovery from a cyberattack can cost millions.
- Reputational damage: Loss of public trust can take years to rebuild.
- Operational disruption: Cyberattacks can halt critical public services.
Pro tip: Regularly review and upskill your IT team’s cybersecurity skills to stay ahead of evolving threats.
Cybersecurity is a survival tool for government agencies
State and local governments face unique cybersecurity challenges, but with the right strategies, tools, and training, they can protect their systems and citizens. By adhering to compliance mandates, implementing a cybersecurity roadmap, and investing in workforce training, agencies can build a resilient defense against cyber threats.
Ready to strengthen your agency’s cybersecurity? Download our Cybersecurity Compliance Checklist for State & Local Governments and explore certifications like Security+ and CySA+ to upskill your IT team today.