 Secure authentication protocols are necessary in today’s constantly evolving threat landscape. Authentication methods have been around for quite a while and are an integral part of an IT pro’s repertoire. Previously, organizations relied on two-factor authentication protocols for verification. Nowadays, multi-factor authentication (MFA) is the industry standard for identity and access verification purposes.
Secure authentication protocols are necessary in today’s constantly evolving threat landscape. Authentication methods have been around for quite a while and are an integral part of an IT pro’s repertoire. Previously, organizations relied on two-factor authentication protocols for verification. Nowadays, multi-factor authentication (MFA) is the industry standard for identity and access verification purposes.
What Is Multi-Factor Authentication?
Multi-factor authentication involves the use of two or more methods or factors of proving and verifying user identity.
Most of us have used a password to log into a resource. This is known as single-factor authentication. In some cases, a password is the only requirement to access the resource you're trying to log into. Following this, you may receive a message via email or an SMS text on your phone, or you might use an authentication application to generate a one-time code. You then input this information to fully log in and access the resource. This is an example of multi-factor authentication, also referred to as second-factor authentication.
Multi-factor authentication is widely used today due to the fact that it improves security for two primary reasons:
- Hackers need to steal more than just your password to take over your identity in order to gain access to resources or accounts. They need to utilize a second attack vector, such as SIM swapping or an email compromise, in order to successfully infiltrate the additional authentication process. Ultimately, this significantly raises the bar when it comes to securing a network because it requires more access controls than just a single-factor password can offer. Multi-factor authentication can also help with ransomware attacks by curtailing lateral movement through networks.
- MFA can also help slow users down and think things through before logging on to a resource.
Three Factors of Authentication
For IT professionals, there are three options for authenticating a person, a device or a process. These factors are the three “somethings,” as shown below.
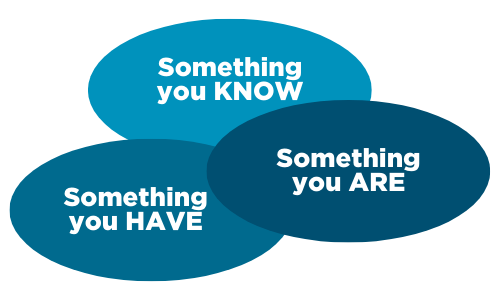
Figure 1: The three factors used in an authentication
The table below contains practical examples of each factor.
|
Factor |
Abstract Example |
Practical Example |
| Something you KNOW |
|
|
| Something you HAVE |
|
|
| Something you ARE |
|
|
Why Multiple Factors?
The primary reason the IT industry employs multiple factors is to ensure thorough verification of access through multiple authentication methods. Often, organizations utilize only two factors for authentication and verification. However, with threat actors persistently finding new ways to bypass single-factor and simpler two-factor authentications, these methods have become increasingly vulnerable. As a result, the implementation of MFA provides a more robust security measure for organizations, despite potentially being more time-consuming and costly. In essence, multi-factor authentication successfully embodies a more proactive approach to security.
Consider a real-life example. Whenever you go to the ATM to withdraw cash, you need to provide two things:
- Your bank card, which is something you HAVE.
- A personal identification number (PIN), which is something you KNOW.
By requiring multiple forms of verification, MFA significantly enhances security measures, making it harder for unauthorized individuals to gain access.
Which Factors Should You Use?
It’s possible to use all three factors or even just two of the three. Most of the time, organizations utilize a combination of something you know and something you have.

Figure 2: The two most often-used factors in MFA
It’s important to note that implementing two of the same factors, such as requiring users to enter two passwords, does not constitute MFA. To be considered MFA, at least two of the three available options must be utilized.
Why Is It Important To Learn About Multi-Factor Authentication?
Organizations who hire IT pros inevitably value two things when it comes to MFA:
1. Understanding and explaining MFA to end users: As a technical support specialist or help desk technician, you will need to effectively communicate how MFA works to those who are new to the concept, as well as troubleshoot when issues arise with the verification process. That’s why the CompTIA A+ exam objectives include MFA as a way to secure wireless networks more effectively.
2. Implementing MFA in various environments: IT pros must be able to successfully implement and integrate MFA across various IT environments, including cloud, data center and on-premises environments. With the prevalence of cloud-first, hybrid environments, MFA should be considered the de facto standard for securing these systems. Consequently, many CompTIA certifications require you to understand MFA as part of implementing authentication and authorization design concepts.
The Role of MFA in CompTIA Certifications
MFA is one of the primary methods used to secure an organization’s cloud presence. As a security analyst, you’ll frequently use vulnerability assessment tools that detect the presence of MFA, which is why the CompTIA Cybersecurity Analyst (CySA+) exam objectives list MFA as a key concept for security operations.
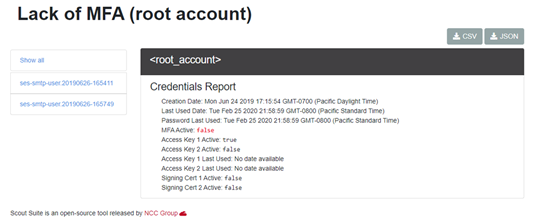
Figure 3: A vulnerability assessment of a cloud implementation
In Figure 3, MFA has not been configured yet. This underscores the reason why more advanced certifications, such as CompTIA Linux+, CompTIA Server+ and CompTIA Advanced Security Practitioner (CASP+), require IT professionals to understand how to implement MFA in various environments.
In addition, most networking devices, ranging from switches and routers to firewalls, are equipped with the capability to support MFA, which is why the CompTIA Network+ exam also assesses your understanding of MFA.
Download CompTIA exam objectives for free.
Want To Learn More About MFA?
Use CompTIA CertMaster Learn + Labs to get deep into MFA. Alternatively, you can create virtual servers in the cloud using platforms like Microsoft Azure, Google Cloud or AWS. Installed virtual environments, such as VirtualBox and VMWare, are also available. By experimenting with this technology on Windows, Linux and networking systems, you can become an MFA expert capable of helping organizations of all sizes enhance their security.
Ready to get started? Learn the skills you need with CompTIA CertMaster Learn + Labs. Sign up for a free 30-day trial today!

