 Global security operations center (SOC) professionals, chief information security officers (CISOs), chief information officers (CIOs), cybersecurity analysts and other IT management roles are constantly battling the growing cyber threat landscape. At the top of the security chain of command are the CISOs, who are consistently keeping data safe, secure and accessible at all times.
Global security operations center (SOC) professionals, chief information security officers (CISOs), chief information officers (CIOs), cybersecurity analysts and other IT management roles are constantly battling the growing cyber threat landscape. At the top of the security chain of command are the CISOs, who are consistently keeping data safe, secure and accessible at all times.
SOCs become critical to helping a CISO ensure all potential security incidents and risks are identified, examined, defended against and reported. With thousands of new adversaries and security vulnerabilities appearing each day, being a security professional can be extremely challenging. As a result, security professionals can face extreme stress and fatigue. Organizations also struggle to update technology, retain employees and hire new talent.
In addition, CISOs and other members of the C-suite may be out of touch with the everyday challenges their SOC teams are facing. Oftentimes, this causes a false sense of confidence when it comes to how well a SOC can respond in the face of a cybersecurity crisis.
According to the Exabeam 2018 State of the SOC report, more than 62% of U.S. and UK security professionals said they would change how their SOC was run. The report dove into the mindset of those in the trenches, as well as those leading them.
6 Ways to Bridge the Divide Between Security and IT Operations
Bridging the digital divide between SOC and IT operations is critical to providing adequate protection from security threats. The following infographic shares the different struggles CISO and SOC professionals face with six things SOC leaders can do right away to amend them, and provides key insights on how organizations can maintain a well-run SOC.
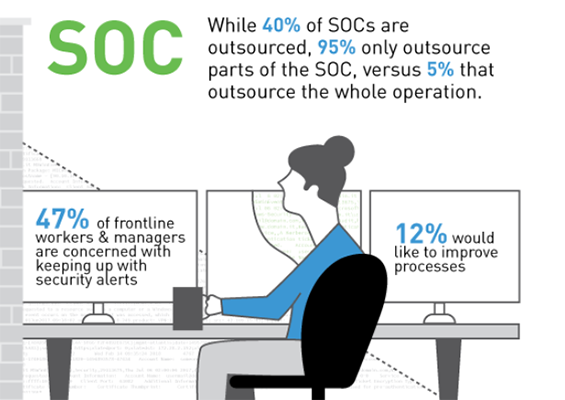
Two Perspectives: The C-Suite vs. the Analyst
For managers, the biggest priorities are on technology, preventative measures and process improvements. Because of this, they are often unaware of security analyst burnout and the struggles they face. When larger issues come about, differing views can become even more pronounced.
Analysts and the C-suite may disagree on the following:
- Staffing issues, such as the amount of experience of particular staff members
- Aging security technology
- General operations and management of day-to-day tasks
- Time spent on documentation and reporting instead of defending the organization
Bridging the Divide
As highlighted by the above infographic, there are several ways to solve the miscommunication between the SOC and C-suite members. Below are some tips for SOC leaders that can be incorporated right away.
- Begin by having open conversations with the analysts.
- “What issues are you facing right now that interfere with your performance?”
- “What would make it easier for you to do your job?
- “How are your recommendations for lessons learned tracked and actioned?”
- “What cooperation do you lack?”
- Have consistent communication with team members.
- Look at where areas of concern are and use it to prioritize your budget.
- Build a relevant incident response (IR) plan.
- Incorporate machine learning technologies.
- Set up the right environment.
Consider implementing a monthly meeting with the SOC to sync on current issues and concerns.
Ask them questions such as the following:
In order to have a productive, healthy working environment, employees of all levels need to be on the same page. C-suite members need to make sure teams are working together during a major crisis. Each team member has their own role, and it is important they know why they are important to the team. Don’t make introductions during a crisis.
Use previous responses to cyber incidents. What inhibited your team from reacting as best as they could? When seeking technical answers, ask what do you want to know and what is presently unknown? Talking to your team members about this can help identify present and future problems from occurring.
First, automate the manual analytical steps. Next, create a step that represents reality – a simplified plan can help establish unity among your staff. A well-thought plan is one with inputs from the entire team and is in the form of a living document. Do not create an IR plan for audit purposes only.
Incorporating artificial intelligence (AI) and machine learning can help eliminate burnout and take away some of the tedious tasks security analysts are responsible for. Well-implemented machine learning allows your organization to “buy” response time and answer the “is this normal?” questions that arise during each incident.
Hire for emotional intelligence rather than what is simply on a technical resume, and ensure the talent you are recruiting has a personality that would fit in well with your existing team. Onboarding should include job shadowing to build a foundation without individual and group assignments. Work products must include a presentation to the larger team. During the entry period, have senior staff regularly share their experiences to help new hires find mentors and build relationships within the team.
Stephen Moore has been vice president and chief security strategist of Exabeam, Inc., since August 2017. Moore has more than 15 years of experience in information security, intrusion analysis, threat intelligence, security architecture and web infrastructure design. Prior to joining Exabeam, Mr. Moore spent more than seven years at Anthem in a variety of cybersecurity practitioner and leadership roles. He was the architect of the new 6,000-square-foot Anthem Cyber Security Operations Center in Indianapolis. Prior to joining Anthem in 2009, he served in a variety of roles at Sallie Mae (now known as Navient and Sallie Mae Bank) within the web infrastructure, program management and information security organizations. He served as staff vice president of cyber security analytics at Anthem, Inc., and played a leading role in the response and remediation of the data breach announced in 2015. He has deep experience working with legal, privacy and audit staff to improve cybersecurity and demonstrate greater organizational relevance. Moore has been a member of advisory board at SecureAuth Corporation since July 2017.


